SuperID certificates
Public Key Infrastructure (PKI) certificates are absolutely necessary in today's connected world. SuperOffice CRM Online requires that all applications support a secure SSL environment. There are various ways to ensure that your applications are able to exchange information with SuperOffice CRM Online in a safe and secure manner.
Certificates are necessary to validate SuperOffice CRM Online issued tokens to partner application for the 3 online environments: SuperOffice Online Development (SOD), Stage, and Production.
The different environments have different certificates used for signing and validating security tokens.
Certificate dependency tree
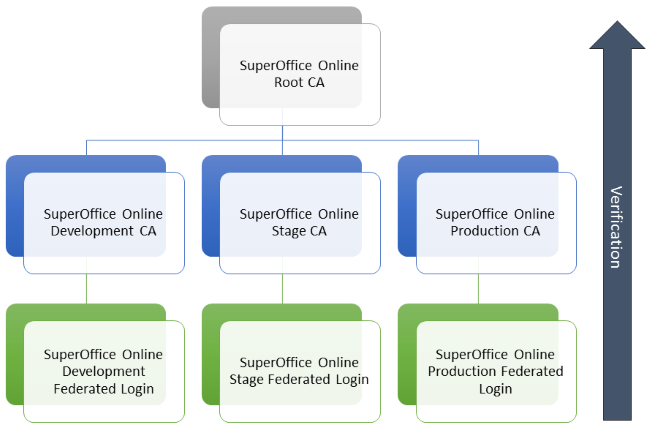
SuperOffice Online Root Certificate Authority (CA) is the root container for all SuperOffice Online certificates.
Environmental certificates establish a trust for their environment of responsibility: Development, stage, or production. Each environmental certificate depends on the SuperOffice Online Root CA and cannot be used without it.
At the lowest level, the subject certificates establish trust for each environment's login services.
- each environmental certificate has a dependency on each federated login certificate
- each federated login certificate depends on its corresponding environmental certificate
Supported trust types
There are 3 main types of certificate trust:
- Chain
- Peer
- None
SuperOffice Online supports both PeerTrust and None.
PeerTrust
The SuperIdTokenHandler class is responsible for validating security tokens. By default, the handler is configured to use PeerTrust.
The handler looks up the source certificate thumbprint in the application settings.
The handler tries to find a certificate with a matching thumbprint in the Trusted People certificate store of the local computer. The source thumbprint must be defined in the application configuration settings.
<appSettings> ... <add key="SuperIdCertificate" value="16b7fb8c3f9ab06885a800c64e64c97c4ab5e98c" /> </appSettings>If a match is found, the next step is to validate the certificate.
If no certificate with a matching thumbprint is found, the ID4037 exception is thrown:
"ID4037: The key needed to verify the signature could not be resolved from the following security key identifier 'SecurityKeyIdentifier."This means that no certificate with a matching thumbprint was found. The only known reasons this might happen are:
- The certificates are not configured correctly.
- There are hidden characters in the value field - such as an "" character.
Note
If you deploy your application in a restricted environment where you don't have access to the certificate store, such as Azure or similar, you can override the default resolver to validate the JWT security token directly instead.